This is a copy of a guide I posted to our local DEFCON group last week. Enjoy.
December 31, 2009
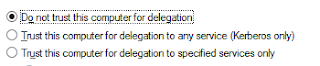
Cracking & Defending a Terminal Server
This is a copy of a guide I posted to our local DEFCON group last week. Enjoy.
December 23, 2009
Trend Micro Ate My Virtual Machine
I had to run some routine security updates for a client yesterday on a host OS running Hyper-V. It was after hours, so I just shut down the two virtual machines and rebooted the physical server after the udpates. When it came back up, I went into Hyper-V Manager and tried to power on my VM's. Low and behold, where there were once two VM's, I now only saw one.
December 07, 2009
If you give a hacker a cookie, he'll ask for a session ID.
Most clients I talk to have a basic understanding that a wireless network should be "secure". They do what they can to make their home and office wireless networks have some semblence of security. However, no one seems to have an issue checking their Facebook account from the local bookstore or pulling up some sensitive company emails at the airport. People make the assumption that since they have no sensitive information on their hard drive and they are running a really good anti-whatever, safety is assured.
I can promise you, it is not. And seeing what you are searching for is not the worse thing that a hacker can do. Let me explain:
I can promise you, it is not. And seeing what you are searching for is not the worse thing that a hacker can do. Let me explain:
December 03, 2009
Google Launches Public DNS
Google may soon start wresting control of another important chunk of the internet. DNS (Domain Name Service) is a critical component of modern networks (including that really big one called the enter-something) and allows you to type in "www.paulhite.com" instead of the cryptic string of numbers that your computer actually uses. Now, having developed it's own presentation protocol (SPDY) and programming language (Go), Google would like to add another course to this meal: Google Public DNS.
Google's proposal is that you should use their shiny new service in place of the DNS servers commonly provided by an ISP. They currently have two IP addresses for you to use:
8.8.8.8
8.8.4.4
The benefit here is that each of these addresses could point to any number of servers, strategically placed throughout the world to give you a decent response time no matter where you are at (theoretically). And since Google already has a great resource from which to pull cached information, their DNS servers should not have to do a whole lot of searching to resolve your forward lookups. The benefit to Google is that they can use unresolved requests to display advertisements instead of traditional error messages. Google claims, however, that the primary concern is increasing the overall speed of the web.
It's all been done before though, the most popular existing service being OpenDNS at the moment. Early test results are showing little improvement with Google DNS over OpenDNS, but the tech-giant is bound to have something enticing planned to go with this service.
Google's proposal is that you should use their shiny new service in place of the DNS servers commonly provided by an ISP. They currently have two IP addresses for you to use:
8.8.8.8
8.8.4.4
The benefit here is that each of these addresses could point to any number of servers, strategically placed throughout the world to give you a decent response time no matter where you are at (theoretically). And since Google already has a great resource from which to pull cached information, their DNS servers should not have to do a whole lot of searching to resolve your forward lookups. The benefit to Google is that they can use unresolved requests to display advertisements instead of traditional error messages. Google claims, however, that the primary concern is increasing the overall speed of the web.
It's all been done before though, the most popular existing service being OpenDNS at the moment. Early test results are showing little improvement with Google DNS over OpenDNS, but the tech-giant is bound to have something enticing planned to go with this service.
November 21, 2009
Nick Wingfield IS the Insider Threat
I perused over this Wall Street Journal article by Nick Wingfield and my heart immediately went out to the poor IT guys at the WSJ who have to put up with him. The title of the article, "Why You Can't Use Personal Technology at the Office", caught my eye because I thought it would be a nice overview of the various reasons bringing your personal techno gadgets to work causes headaches for your IT department. As it turns out, Nick was simply using the WSJ as a soapbox to cry his heart out about having to use "ancient" technology like "Windows XP" and how clever he is to have found a way around his companies IT policy enforcement to install his favorite toolbars and plugins. How he got a job at the WSJ writing about technology is beyond comprehension (I have a few ideas), but at least he gave me a good example of someone with just enough technical know-how to skate around corporate policies and not enough common sense to see how dangerous that is.
November 20, 2009
Bad Tech Advice, Pt. 1
I had other items to write about, but my fury at having to deal with astonishingly bad tech support, advice, or recommendations is at a boiling point. It's not the inexperience or naivety that bothers me, we all have to start somewhere and some of us still struggle with new technology. It's the fact that these people, or companies, sell themselves as "experts"; after which I have to explain to the client that they would have gotten more from their money by investing in one of the many wonderful business opportunities available in Nigeria.
November 18, 2009
How I Learned to Stop Worrying and Love the Cloud.
Despite deep-seated childhood fears of all data being consolidated into a single powerful system that touches everything, a little research (and extensive therapy) helped me to develop a healthy relationship with "cloud computing". And by that, I mean that nearly everything I do is contained in the cloud and I am completely dependent on it. Healthy is a relative term.
November 15, 2009
Google Knows How Smart We Isn't
I stumbled across a very brief blog post concerning Google search suggestions and how they reinforce the idea of "txt speak" being associated with immaturity and generally less-than-stellar decision making skills. I thought I might expound on this with some screenshots.
Microsoft Declares Ownership of 'sudo'; rest of world
Some clerk at the US Patent Office apparently had a seizure and scribbled his approval across this blatantly monopolistic patent for a "Rights Elevator" filed by Microsoft in 2005. Here's the abstract:
In Microsoft's defense, the patent indicates that they are improving on existing technologies. The patent was filed around the same time Vista was being defecated developed along with UAC. What really concerns me is the second sentence that states this "rights elevator" GUI will "identify an account having a right to permit a task". So essentially, if I'm Joe User trying to install the latest "Free Smiley Pack with Screensavers" application on my corporate network, but lack the permission to do so, my handy "rights elevator" will simply identify the username of an account that does. This seems like an unnecessary (and potentially insecure) feature to me, but I suppose that's Microsoft's modus operandi at this point.
Systems and/or methods are described that enable a user to elevate his or her rights. In one embodiment, these systems and/or methods present a user interface identifying an account having a right to permit a task in response to the task being prohibited based on a user's current account not having that right.
In Microsoft's defense, the patent indicates that they are improving on existing technologies. The patent was filed around the same time Vista was being defecated developed along with UAC. What really concerns me is the second sentence that states this "rights elevator" GUI will "identify an account having a right to permit a task". So essentially, if I'm Joe User trying to install the latest "Free Smiley Pack with Screensavers" application on my corporate network, but lack the permission to do so, my handy "rights elevator" will simply identify the username of an account that does. This seems like an unnecessary (and potentially insecure) feature to me, but I suppose that's Microsoft's modus operandi at this point.
Subscribe to:
Posts (Atom)
Red Flags and the Value of Experience
One of the things I hear often said, and something I subscribe to as well, is the idea that a lot of technical knowledge in the world of IT ...
-
Because I'm a glutton for punishment, I recently started rolling out System Center Configuration Manager 2012 R2 SP1 and System Center E...
-
UPDATE: Turns out this is a known issue during the 1.5 > 5.1 VSM upgrade and a fix should be released in an upcoming patch. That's ...
-
Having repeated this nightmarish migration several times now, here's the steps I've found to be most efficient: Import your XenSer...

